The Facebook-owned mobile messaging service WhatsApp is finally rolling out the document sharing feature to iOS and Android apps (the feature is unfortunately limited to only PDF files at this time). A...
Why was AMP created? Access to information is at the heart of Google’s mission. When it comes to speed, the mobile web isn’t living up to the expectations people have...
Beginning January 12, 2016, only the most current version of Internet Explorer available for a supported operating system will receive technical support and security updates. Internet Explorer 11 is the...
CSS stands for Cascading Style Sheets and it describes how HTML elements are to be displayed on screen. CSS is used to define styles for your web pages, including the design, layout...
Website size has increased about 25 percent from 2014 - today's website is averaging 2162 KB and it's showing no signs of stopping. In the past five years, websites have...
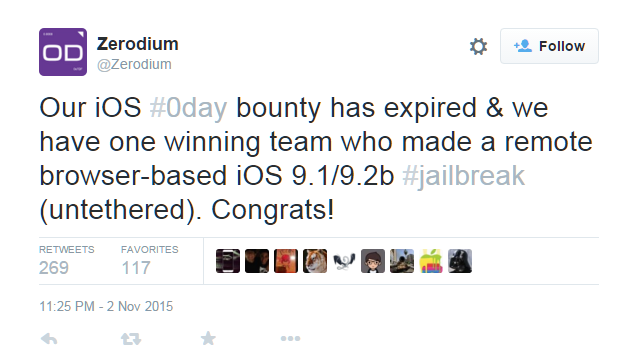
Last month, a Bug bounty challenge was announced by Zerodium for finding a hack that must allow an attacker to remotely compromise a non-jailbroken Apple device through: A web page...
Android devices are know to experience serious security problems. Most of the Android malware is outside the Google Play Store but the biggest problem is that many Android devices don’t...
According to an Adobe Security Bulletin, a critical vulnerability (CVE-2015-7645) has been identified in Adobe Flash Player 19.0.0.207 and earlier versions for Windows, Macintosh and Linux. This zero-day exploit can cause...
JPEG images may soon have copy protection! The Joint Photographic Experts Group recently launched a Privacy & Security initiative that potentially brings digital rights management (DRM) to regular JPEG images,...
Some of the most common problems that people face in Social Media is the size of images, both branding and those to be shared. Here's a list of the specific...
Smartphones have only been around for about ten years, but myths have still built up over time. Some of these myths just won’t go away, exactly like PC myths don't...
Myths and urban legends regarding PCs built up over time, passed from person to person. Some have a grain of truth, but are no longer true due to technological progress. Hackers Are...